NMap Basics
I’m going to break down how to use NMap. We’ll start with setting up an environment on VirtualBox and work through some basic commands and how those commands help towards that greater goal of information security and compliance.
Environment — Let’s keep it simple:
*We are installing Kali Linux on an Oracle VirtualBox and working with this environment going forward.
- Download VirtualBox from Oracle if you do not already have it installed.
- Download Kali and follow these detailed instructions if you run into a snag.
- Start your Kali VM and log into your system using the username: kali and the password: kali. There are some distributions that advertise the default username: root and password: toor. One of these should work.
Running Basic Nmap Commands:
Nmap is a tool that helps information security analysts get a picture of what a network looks like. To get started, open the terminal on your Kali machine and type nmap -help. You should see a list of capabilities that Nmap provides, and this is a handy place to look if some of the command vocabulary trips you up later. For a more detailed guide-book, check out the NMap reference guide.
Nmap provides an example web application called scanMe.nmap.org that you can use as a target to try out basic commands on. Keep in mind that scanning targets without explicit permission is not ethical, so in the examples below I will use my own machine or the target supplied by NMap. For more detail on how scanning ethics have played out in real-life, check out the NMap legal issues page.
Enter ‘nslookup scanme.nmap.org’ in the command line. You will see that nmap has scanned the target, in this case the scanme web application. The service has returned some basic details.

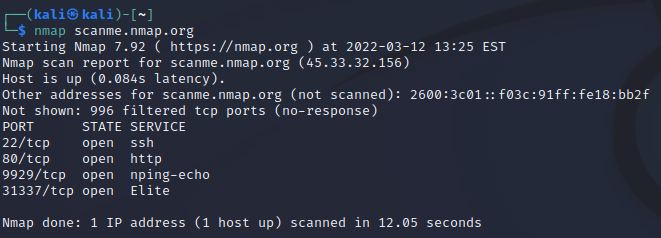
You can get a little more detail by typing ‘nmap scanme.nmap.org’. Using the same target, we are now able to see which ports are currently being utilized at this specific IP. You can see that this application is utilizing SSH, HTTP, NPing, and Elite ports. This shows us that there is traffic here, but it doesn’t reveal much else.
I can go further and scan my home network using ‘nmap -oG — (my ip address range here) -vv > /home/kali/Desktop/localScan. The -oG flag means the results of the scan will be exported to a grepable format. The target of this scan is my IP address between .15 and .255. ‘vv’ indicates that I want a verbose response and ‘> /home/kali/Desktop/localscan’ indicates that I want my grepable file to be saved on my desktop with the name ‘localscan’.

The results of my scan are now stored in a file and the information I receive indicates that port 243 is currently up and running. This portion of the report shows that only one host is up and running on 10.0.2.15.

Let’s dig a little deeper and go for an aggressive scan. Running nmap -A will return information about the operating system that a target is running. Using the scanme.nmap.org target, this is what you should see.

You can see here that scanme.nmap.org is running Ubuntu 2.13, Apache 2.4.7, and Linux-Kernel. To get an idea of which ports are being utilized, we can run ‘nmap -F scanme.nmap.org’. This will scan the most common 100 ports and operates much faster (-F) than a complete scan. This scan results show us that ssh and http traffic are currently running on this IP.

That sums up a few basic commands using NMap. We learned nslookup, basic nmap scans, -oG, -vv, -A, and -F. As a starting point, consider the CEH scanning methodology guide. We have really only worked through the first two points on the checklist.
Check back next week and I’ll break down what we can do with this information moving forward.
